In the landscape of 2025, names like SolarWinds and Log4j are no longer just headlines—they are permanent scars on the industry. These events made one reality crystal clear: securing how code moves from a developer’s laptop to a production environment is no longer optional. It is table stakes for modern digital resilience.
The common reaction is to layer on more complexity: buy a dedicated SBOM tool, install a separate signing appliance, and contract a niche “supply-chain security” startup.
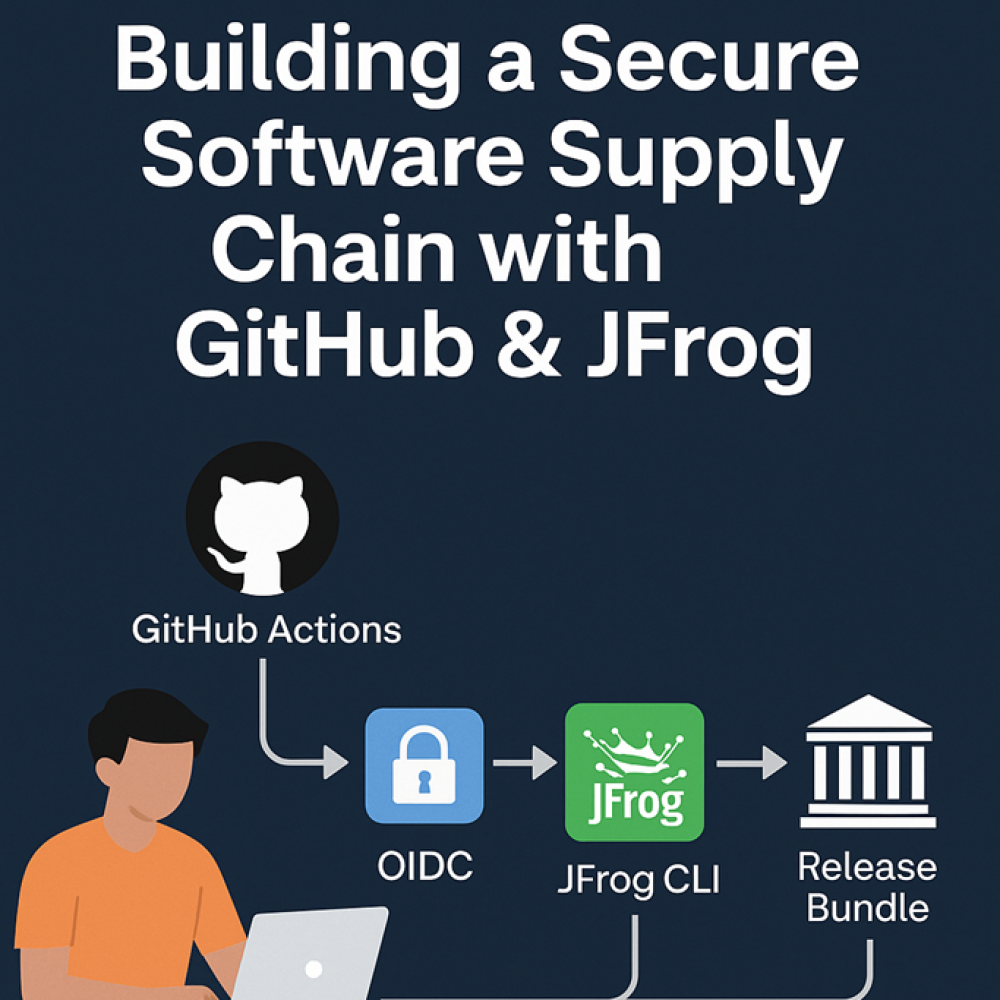
At TL Consulting, we believe there is a more pragmatic, architectural approach. You can achieve an extremely strong, auditable, and automated secure supply chain using only two commercial platforms that most enterprise teams already possess: GitHub and JFrog.
Here is the complete, production-ready blueprint that we see leading enterprises adopting today.
The Tooling Matrix: Doing More with Less
Many organisations unknowingly sit on a goldmine of security features. Rather than procuring new tools, we recommend mapping your critical supply chain requirements to your existing ecosystem.
- Source of Truth: GitHub Repositories (Code versioning and protection)
- CI/CD & Evidence: GitHub Actions runs the logic; JFrog CLI captures the evidence.
- Attestation: GitHub OIDC authenticates the build; JFrog BuildInfo locks it.
- Scanning: GitHub Advanced Security scans source (SAST); JFrog Xray scans binaries (SCA).
- Verification: Artifactory Policies block bad downloads based on scan data.
Prerequisites
Before implementing the pipeline below, ensure you have:
- OIDC Integration configured between GitHub and JFrog to eliminate long-lived static credentials.
- Xray Watches configured with “Block Download” enabled for critical violations.
- GPG Signing Keys managed within the JFrog Platform.
The Core Principle: Chain of Custody
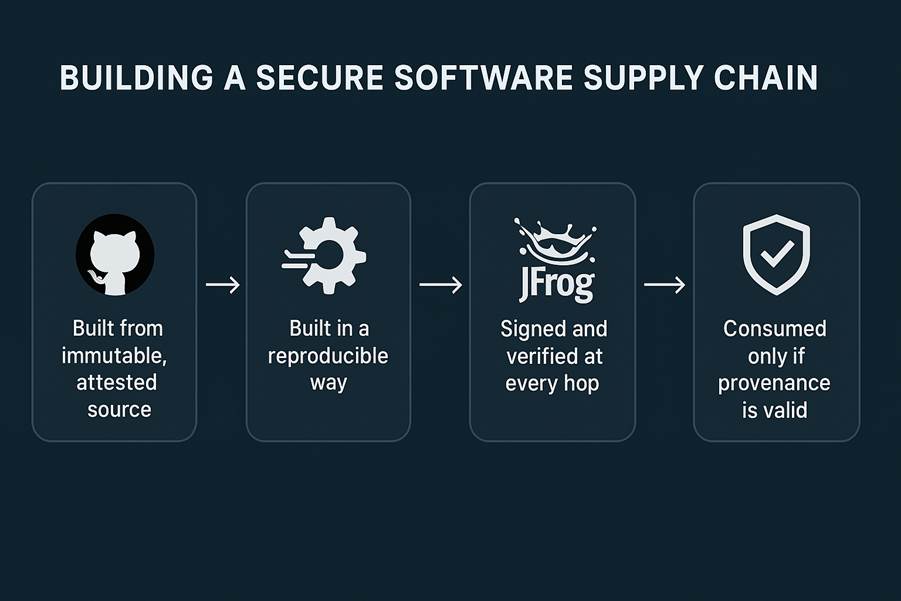
To achieve true security, we must stop treating the pipeline as a “dumb pipe” and start treating it as a chain of custody. Every artifact that flows through your pipeline must satisfy four conditions:
- Built from immutable, attested source (GitHub)
- Built in a reproducible way (GitHub Actions + JFrog CLI)
- Signed and verified at every hop (JFrog Xray + Artifactory + JFrog Signing)
- Consumed only if provenance is valid (Artifactory policy enforcement)
The secret sauce in this architecture is the modern JFrog CLI (jf). It doesn’t just upload files; it collects environment variables, git commit hashes, and dependencies to create a tamper-proof BuildInfo object.
The 2025 Secure Pipeline Workflow
Zero-Trust Consumption: The Registry Gate
Security isn’t just about building safely, it’s about ensuring only safe things run.
If Xray finds a vulnerability after the build (e.g., a brand new CVE is discovered in an image you built last month), Artifactory can be configured to return a 403 Forbidden when Kubernetes tries to pull that image.
The Result: When a cluster tries to pull a vulnerable image, the pull is denied at the registry level. No cluster-side security agents are required to block it.
Common Pitfalls We See in the Field
At TL Consulting, we often help teams remediate failed implementations. Here are the top mistakes to avoid:
- Not Collecting Environment Data Early: Running metadata collection after the build often results in missing context. Always run
jf rt bceimmediately after checkout. - Missing the Signature: Creating Release Bundles without the
--signflag defeats the purpose of tamper-proofing. - The “JFrog Build” Confusion: There is no
jf docker buildcommand. You must use standarddocker build, followed byjf docker pushto capture the dependencies correctly.
The Bottom Line
You don’t need a dozen vendors to secure your software supply chain.
If you are already paying for GitHub Enterprise and JFrog Artifactory + Xray, you possess 95% of the capabilities that the Fortune 500 are scrambling to buy from niche startups. By connecting the dots correctly—Immutable source, Attested builds, Signed artifacts, and Verified consumption—you can build a secure supply chain that withstands nation-state attacks, without increasing your vendor spend.
Ready to lock down your pipelines? TL Consulting specializes in optimizing DevOps toolchains for security and efficiency. If you need help implementing this pattern or auditing your current supply chain, contact us today.