“Shift Left” Application Security in Kubernetes with Open Policy Agent (OPA) and Tanzu Mission Control (TMC)
To secure a Kubernetes environment, we must adopt the “shift left” security approach right from the initial phases of the development, rather than wait for the deployment to complete and focus on the security at later stages of the build.
Kubernetes security is constantly evolving with new features to strengthen both the application and cluster security. Kubernetes offers several mechanisms to administer security within the cluster. Some of these include enforcing resource limits, API security, standardizing containers, auditing and so on.
Here we will discuss one of such mechanism, which helps to implement the shift left security in a Kubernetes cluster.
What is OPA?
Open Policy Agent (OPA) is an open-source policy engine that provides a way of manifesting the policies declaratively as code, which helps to ease out some of the decision-making processes with the Kubernetes cluster end users, such as developers, operations teams without impacting the agility of the development.
OPA uses a policy language called Rego, which allows you to write policies as code for various services like Kubernetes, CI/CD, Chef, and Terraform using the same language.
OPA enforces the separation of concern by decoupling the decision-making from the core business logic of the applications.
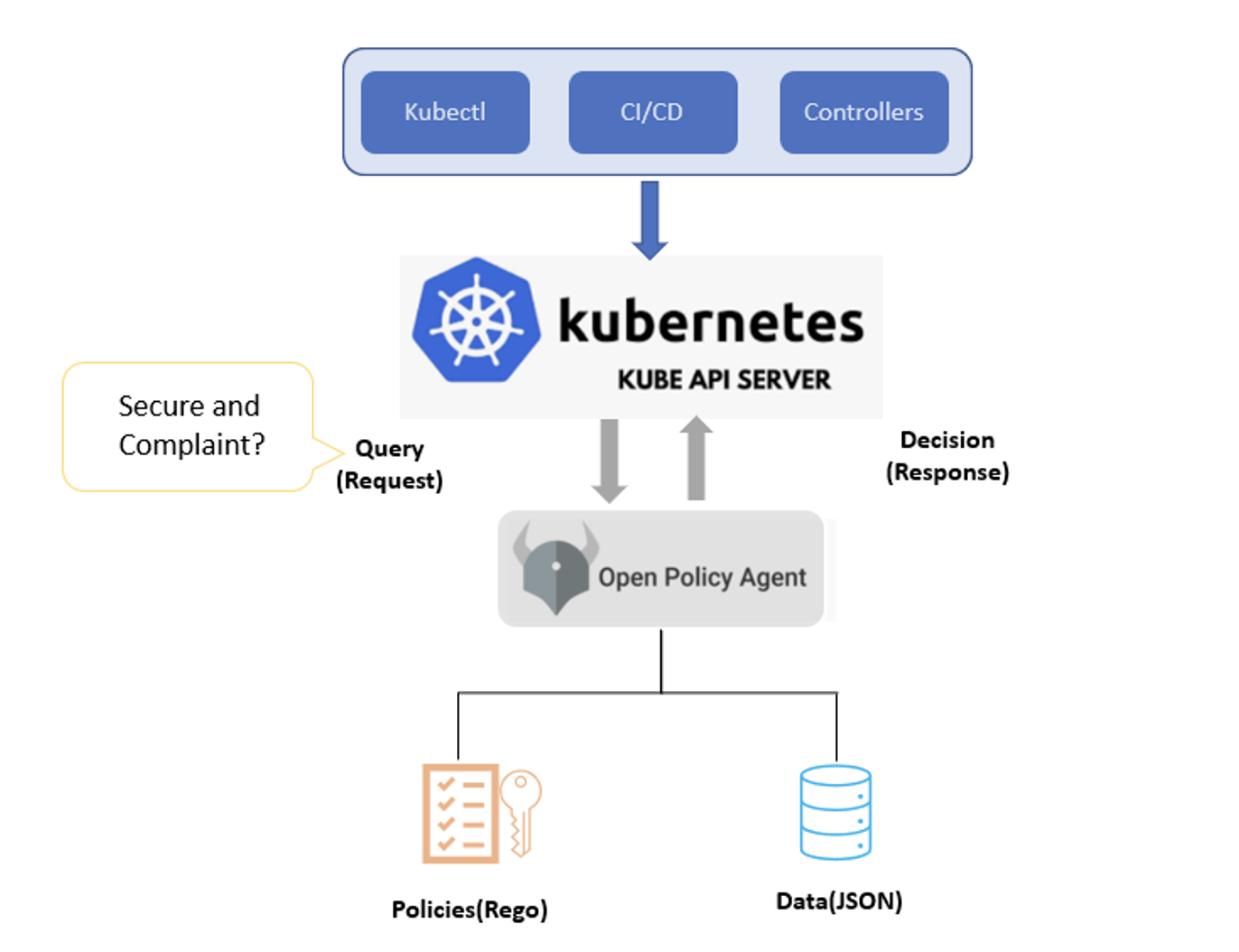
OPA Workflow:
OPA provides centralized policy management and generates policy decisions by evaluating the input data against policies (written in Rego) and data (in JSON) through RESTful APIs. Here we have some of the example policies we can enforce using OPA:
- Which users can access which resources?
- Which subnets egress traffic is allowed to?
- Include node and pod (anti-), affinity selectors, on Deployments
- Which clusters a workload must be deployed to?
- Ensure all the images come from a trusted registry
- Which OS capabilities a container can execute with.
- Implementing Kubernetes Admission Controllers to validate API requests.
- Allowing or denying Terraform changes based on compliance or safety rules.
- Enforcing certain deployment policies (such as resource limits, meta data types of resources)
Creating Custom Policies using OPA in Tanzu Mission Control (TMC)
VMware Tanzu Mission Control is a centralized hub for simplified, multi-cloud, multi-cluster Kubernetes management.
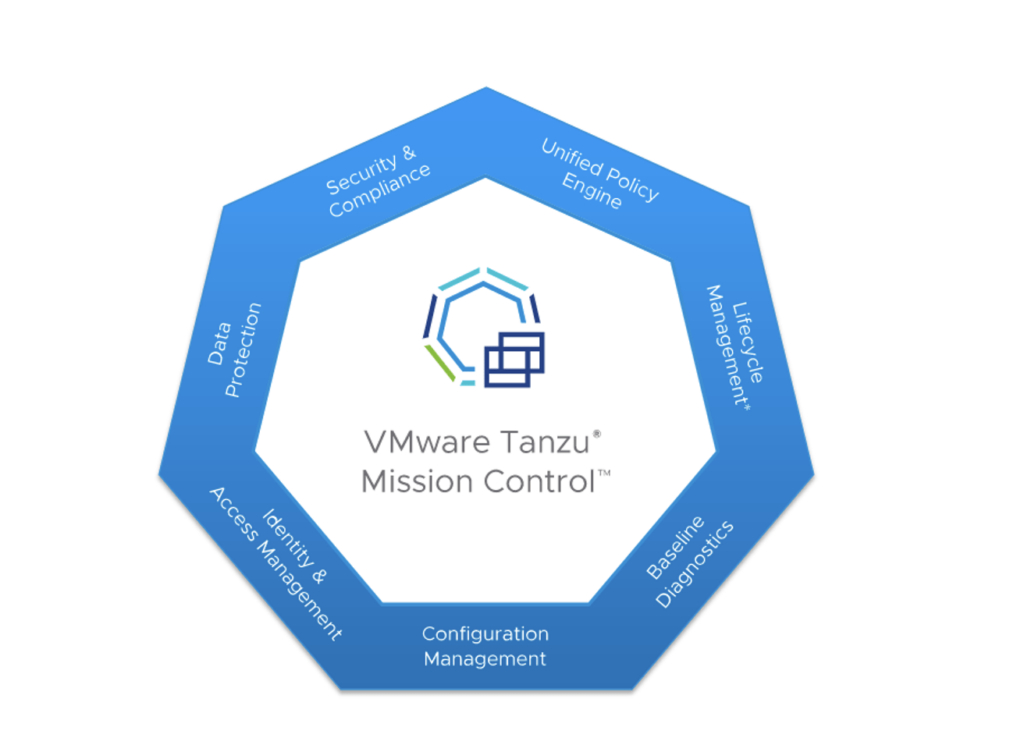
Tanzu Mission Control aims to help with the following list of Kubernetes operations:
- Managing clusters on both public, private cloud and edge
- Cluster lifecycle management on supported providers
- Manage security across multiple clusters
- Centralized policy management
- Access management
- Cluster conformance
VMware Tanzu Mission Control provides centralized policy management for specific policies that you can use to govern your fleet of Kubernetes clusters, The polices include access controls, image registry policies, and resource limit policies. While these cover the baseline polices, it also offers an ability to create custom policies using Open Policy Agent (OPA). Custom policies are somewhat open-ended and provide the opportunity to address aspects of cluster management that specifically suit the needs of your organization.
As described above OPA implement specialized policies that enforce and govern your Kubernetes clusters.
Closing thoughts:
Enterprises use the OPA to enforce, govern, audit, and remediate policies across all IT environments. You can use OPA to centralize operational, security, and compliance aspects of Kubernetes, in the context of cloud-native deployments, (CI/CD) pipelines, auditing and data protection.
Thus, OPA enables DevOps teams to shift control over application authorization further left to advance the adoption of best DevSecOps practices.
TL Consulting
TLConsulting brings its consulting and engineering personnel to application modernisation adoption and implementation by providing range of services – as If you need assistance with your Containers/Kubernetes adoption, please contact us at our kubernetes consulting services page.