Embrace DevSecOps
Author: Ravi Cheetirala
Technical Architect ( Cloud & DevSecOps) at TL Consulting
DevOps is a widely adopted cultural norm in modern software development. It enabled enterprises to bring development teams, operations teams and tools under a single streamlined process. In addition, its automation capabilities help organisations to deliver the software much faster, by reducing the costs and release cycle times. However, in many cases security is not prioritised as a part of the CI/CD practices, thus the move to DevSecOps has not been adopted.
While DevOps has been a successful methodology, one of the key roadblocks is that it doesn’t stress much upon a security and governance lens, as its core focus is on agility and faster time to market.
A recent survey conducted by GitLab, (one of the popular DevOps vendors) had proven the point that more than 70% organisations have not included security in their DevOps model.
With the rise of cyber-attacks, most of the incidents occur by exploiting the vulnerabilities in the software, which indicates a compelling need of rearchitecting the existing DevOps model to DevSecOps by adding additional levels of security and governance.
Market Insights on DevSecOps adoption
As per the recent survey by Gitlab conducted in the fall of year 2021. Please find some of the insights on DevOps, and security.
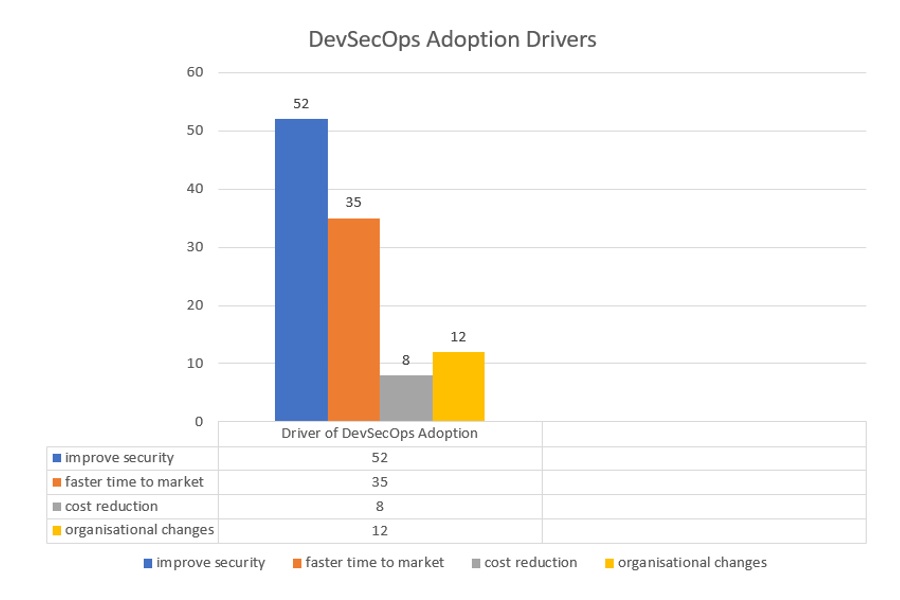
The chart below illustrates the various drivers to adopt the DevSecOps. These findings demonstrate the alignment of improved security as a top priority for DevSecOps enablement.
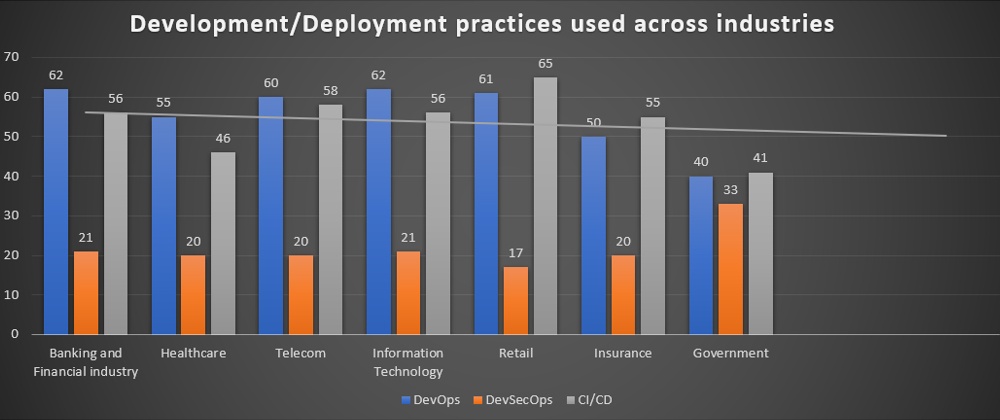
Why do we need DevSecOps?
As per the above market insights, it is evident that more than 50% of the organisations have chosen security as their primary driver to lead to adoption. This is due to the fact conventional security measures are not good enough to cope up with latest technology innovations. Hence there is pressing need of DevSecOps adoption to have high security measures.
What is DevSecOps?
DevSecOps is an extension of DevOps by adding additional measures on security and governance layers, such as security testing, observability and, governance. Just like DevOps, the goal of DevSecOps is to deliver the trusted and secured software faster.
Security adoption barriers in DevOps:
- Developers are focused on acceleration, least bothered about security – With the DevOps adoption, developers deliver the software faster. However, they tend to ignore the best security practices. Some of the risks include using an unsolicited third-party /open-source software downloaded from the internet without much of scrutiny and consent.
- Conflicting interests between teams – Development teams are usually relying on other teams for security and vulnerability testing, which is usually planned as a separate phase of the project. The delivered software might pose multiple security threats, vulnerabilities and usually, security analysts are assigned to review and take care of these issues. These usually create a knowledge gap between teams, thus end up delivering a compromised software.
- Cloud and container security challenges – Undoubtedly the wide adoption of containers and public cloud environments are helping in exceptional productivity with low cost and innovation lens for the organisation, however it also brings new security risks and challenges. For instance, containers are an operating system agnostic and that can run applications anywhere, but the lack of visibility into containers makes it difficult to scan them for vulnerabilities.
- Lack of skills and knowledge on security – There are fundamental knowledge gaps on security frameworks as most of the security standards are industry specific. Which acts as a barrier to achieve higher degree of efficiency with devops.
- The pitfall of DevOps nature – The core nature of DevOps is collaboration of the teams. This interconnection allows us the sharing of privileged information. Teams share account credentials, tokens, and SSH keys. Systems such as applications, containers, and microservices also share passwords and tokens. This opens an opportunity to attackers to disrupt operations, and steal information.
How to implement DevSecOps?
- Embed Security in the pipelines – Implement security in the DevOps or CI/CD pipelines as an additional level of integration, such as including the DAST, SAST and vulnerability, image scanning tools, which would help to identify and resolve the code vulnerabilities as soon as they appear.
- Identify the compliance requirements at design stage – Understand the organisation security framework and compare with the industry’s security guidelines during the early stages of design. This gap analysis will help us to assess the right tools to choose for automation.
- Shift left security approach – Embedding the security in the early stages of development cycles. As we move along to various phases of the development process, security will be carried along instead of focusing on the end. This leads to a better outcome and lesser challenges. Shift left is a preventive approach rather a reactive one.
- Automate as much as possible – The cornerstone of the DevOps is automation, use those capabilities to automate the security and governance by integrating with right tools in the CI/CD pipelines. DevSecOps tooling needs to run with full automation without any manual interventions.
- Validating cloud /container security standards – As a best practice, it is good to evaluate the cloud security standards with organisational, industry security frameworks and identify the gaps in the early stages. This will ensure the early detection of threats and organisational alignment.
- Creating awareness and education – Clear delineation of roles and responsibilities, creating the awareness of security best practices, providing education on industry security framework. Establishing a safe code guideline from the security lens. Adopting a security tooling is not always the best solution, as it might be ineffective if the teams do not know on how to use it.
- Establishing a governance model – Creating a governance model is the vital part of implementing the devsecops model to get the maximum outcome. Adopt the observability and governance tools, which will help to create a transparency in the teams to identify and address the security and other application related issues reported at all levels.
How does DevSecOps fit in organisational GRC framework?
GRC (Governance, Risk management and Compliance) and DevSecOps use various skills, tools and processes. However, their core objectives are aligned, and both the teams can collaborate and appreciate each other. DevSecOps is more focussed on IT front on application delivery and automation, however it should fit in the broader context of organisational GRC framework.
The capabilities and outcomes by the DevSecOps complement the GRC framework. End goal of these processes is to deliver efficient, complaint, and secure software to their customers, which will improve their growth and prospects.
Some of the tools available in marketplace, used in DevSecOps:
- SonarQube: used for code quality, vulnerability review and technical debt computation.
- CheckMarx: a complete suite of software security solutions. This suite provides security testing for static and dynamic applications, tools like software composition analysis, and code bashing to promote software security culture among developers.
- Fortify: provides application security as a service. It is used majorly in enterprise for Secure development, security testing, and continuous monitoring and protection.
- HashiCorp Vault: It manages the secrets like passwords, tokens, API keys, certificates, and protect such sensitive information.
- IriusRisk: provides production-level application security at scale. It helps you manage threat models and security risks using two-way synchronization with testing tools and issue trackers with a real-time security activity view.
- JFrog Xray: It scans the builds, artifacts, and container images for security vulnerabilities and licensing issues in the dependencies.
Conclusion
Evidently, living in the era of DevOps has brought certain new challenges, including a rapid surge in cybersecurity attacks and threats from the attackers are undebatable. Recognising the need of adopting a stronger security and compliance framework is the starting point of embracing the DevSecOps, which will drive us towards achieving better security outlook for the enterprise.
If you want to find out more, please review our DevSecOps services page or contact us below.
